What is cloud security?
Security is a crucial aspect of any IT infrastructure, especially for sensitive data such as healthcare or banking data. AWS offers a resilient and secure infrastructure through its many services that ensure high levels of security and compliance.
To ensure this security, Amazon invests heavily in innovation and research and development, with a budget of $22 billion in 2018. Networks are secured with built-in firewalls and on-the-fly data encryption. In addition, connections are dedicated in the form of high-speed dark fibers, which helps mitigate DDOS attacks through edge computing.
Furthermore, AWS offers deployment, inventory, and configuration tools to ensure infrastructure compliance and ensure that everything is configured properly. These tools include a security model definition and management tools that enable server compliance.
Through these many tools and services, AWS offers a secure and resilient infrastructure that allows for sensitive data to be stored securely, ensuring the confidentiality and compliance of the infrastructure.
Security principles
To ensure this security, it is essential to put policies and tools in place to control access to data, trace actions, and limit the human factor.
It is important to identify who accesses what, when, and at what level, by implementing identification and traceability tools to ensure the security of data in transit and at rest. It is also essential to automate tasks to limit the human factor and ensure infrastructure compliance.
To ensure the security of the infrastructure, it is important to stay up to date, apply new tools and services, and configure the network securely. Amazon provides many tools to facilitate these tasks and help users comply with security standards.
The responsibility for cloud security is shared between AWS and users, with AWS responsible for cloud security and users responsible for everything in the cloud. To facilitate the implementation of security policies, Amazon offers configuration, data encryption, and access control tools to ensure infrastructure security.
OSI model
| # | Layer | Application | Description |
|---|---|---|---|
| 7 | Application | Data | Enables communication between the application and the network |
| 6 | Presentation | Data | Manages data representation (SSL encryption) |
| 5 | Session | Data | Manages communication between hosts |
| 4 | Transport | Segments | Manages end-to-end reliability and connection |
| 3 | Network | Packets | Manages logical addressing and path determination |
| 2 | Data link | Frames | Manages physical addressing |
| 1 | Physical | Bits | Manages multimedia, signal, and binary transmission |
Then, the data link layer divides the data into frames, which are sequences of bits encapsulating the packets. The Network layer fragments the data into smaller packets and encapsulates them. Finally, a packet encapsulates segments to form a set of data. It's like Russian dolls, the data are nested inside each other.
Security Recommendations
- Use multi-factor authentication (MFA) with every account.
- Use SSL/TLS to communicate with AWS resources.
- Configure API and user activity logging with AWS CloudTrail.
- Use AWS encryption solutions, as well as all default security controls within AWS services.
- Use managed security services like Amazon Macie, which helps discover and secure personal data stored in Amazon S3.
- Each subnet should be associated with a route table, which indicates the allowed routes for outbound traffic leaving the subnet. Every subnet you create is automatically associated with the main route table of your VPC.
- A security group (stateful) acts as a virtual firewall for your instance to control incoming and outgoing traffic.
- A security group does not act at the subnet level.
Network Access Control List (NACL) Checklist
Access control lists (ACLs) are an optional security layer for Amazon VPC networks, which act as a firewall to control incoming and outgoing traffic from one or more subnets. Unlike security groups, ACLs are stateless, which means that responses to allowed inbound traffic are subject to outbound traffic rules (and vice versa). A custom ACL can be created and associated with a subnet, and by default, every ACL denies all incoming and outgoing traffic until you add rules. It is important to note that ACLs work at the instance level, while security groups work at the network level.
Conducting Penetration Testing:
It is possible to test the AWS environment against defined security standards. But only for the following services:
- Amazon EC2 instances, NAT gateway, and Elastic Load Balancer
- Amazon RDS
- Amazon CloudFront
- Amazon Aurora
- Amazon API Gateways
- AWS Lambda and Lambda Edge functions
- Amazon Lightsail resources
- Amazon Elastic Beanstalk environments
It is also prohibited to:
- Perform DNS zone inspection via hosted zones on Amazon Route 53
- Conduct DoS, DDoS, simulated DoS, and simulated DDoS attacks
- Port flooding
- Protocol flooding
- Request flooding (connection and API request flooding)
Identity and Access Management (IAM)
IAM is a service that allows for centralized, secure management of users and groups through multi-factor authentication (MFA). It allows for sharing of AWS account access among different entities and offers granular control over permissions. IAM offers federated entities with a directory such as Windows, Facebook, etc. and allows for password rotation and security management. IAM manages authorization and denial through policies.
IAM is like a conductor. When you first log in, you start with a root account, which is the super-user with all rights. This should be handled with care. IAM offers granularity of permissions and possible actions, the ability to create users, groups, roles, policies, and so on.
It is possible to create an administrator group, add users to it, and then create a policy to manage access and permissions to resources. IAM also allows for creating user profiles that provide console access, for which the user must enter a username and password, access keys (ssh/API) with an Access Key Id and secret access key, as well as multi-factor authentication (MFA).
Role
IAM roles are a set of policies that can be associated with a user, a group of users, or a service. They allow for temporary authentication methods to be assigned to resources, which generates a new identifier each time.
For each role, we must define an approval policy (Trust policy), which authorizes an entity to assume the role via authentication, and an authorization policy (Access policy), which associates permissions with the role.
When should we create an IAM user instead of a role?
- You have created an AWS account, and you are the only one working on it.
- Other people in your group need to work on your AWS account, and your group does not use any other identity mechanism.
- You want to use the command line interface (CLI) to work with AWS.
When should we create an IAM role instead of a user?
- You are creating an application that runs on an EC2 instance and makes requests to AWS.
- You are creating an application that runs on a mobile phone and makes requests to AWS.
- Users in your company are authenticated in your corporate network and want to be able to use AWS without having to log in again.
Best practices:
- Never use the root account and never share its access.
- Use an IAM administrator to perform all actions.
- Follow IAM recommendations: remove access keys from the root account, enable MFA, create users with console access or programmatic access, use groups to assign permissions, use roles for temporary access, and apply an IAM password policy.
- Attention: root accounts have no restrictions and are a free service.
Policies
A policy is a text file in JSON format. Each line provides permissions for different resources and provides:
- The principal: designates one or more existing entities, knowing that an entity is designated by an ARN (Amazon Resource Name). An ARN is an identifier that identifies a resource.
- The action: describes the type of access authorized or denied.
- The resource.
- The condition: lists the criteria that must be valid to authorize an action.
Federated Identity
Federated identity does not allow the use of an ARN. If our users are internal to our company, which has 600 users, we can use a proprietary broker that is compatible with the SAML 2.0 standard, which allows for the exchange of security data between domains. Our directory can identify itself directly to our AWS resources via the AWS Directory Service.
We can use external providers such as Google, Facebook, etc. for authentication.
AWS Organizations
AWS Organizations allows for control over access, compliance, security, and billing, as well as the sharing of resources across all of your AWS accounts in a centralized manner. For this, we have many different tools available, and we can control via:
- The console
- The command line
- The software development kit (SDK)
- HTTPS API calls
The creation steps are as follows:
- Create the organization with the root account.
- Create the organizational units to which we can apply control policies (SCP).
- Test the policies of our organization (for example, by creating a policy that prohibits any action in CloudTrail).
- Monitor important changes in our organization by:
- Configuring an event selector in CloudTrail.
- Configuring a Lambda function.
- Creating an Amazon SNS topic that sends emails and SMS messages.
- Creating a rule for events in CloudWatch.
- Testing our CloudWatch event rule.
AWS Cloudtrail
AWS CloudTrail allows you to log, continuously monitor, and retain activity in your AWS account for your entire AWS infrastructure. All logs are stored, and this service allows you to trace all actions. It offers the following benefits:
- Simplification of compliance.
- Troubleshooting and security analysis based on logs.
- Visibility into user and resource activity.
- Security automation.
It is used for:
- Assisting with compliance.
- Analyzing security.
- Detecting data exfiltration.
- Resolving operational issues.
- Detecting unusual activity.
Security, Identity, and Compliance
The common point of these three themes is the user who has the means of intervention via:

These are all the entry points of our services. There are 3 ways to verify actions:
Logs
- With logs we can detect and alert
- We then have a view of what's happening
- We can represent the infrastructure like this:
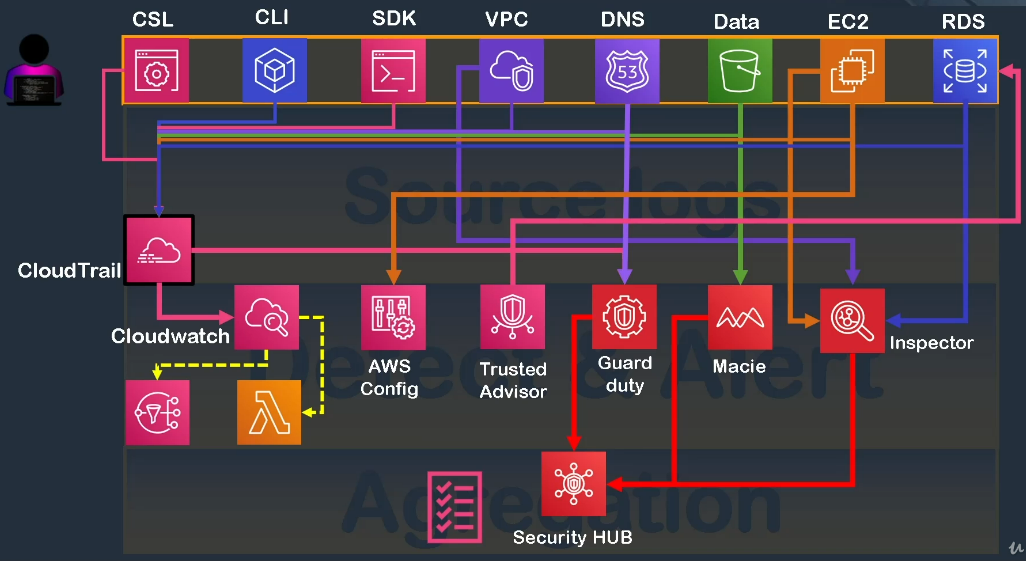
Here is an overview of the different security services offered by AWS:
- CloudWatch: allows for SMS alerts and scripting of actions.
- GuardDuty: verifies the source and compliance of incoming data.
- AWS Config: allows for the configuration of alerts.
- Inspector: service for running cycles to perform audits.
- Macie: allows for processing of data to ensure data exposure isn't happening.
AWS Directory Service
AWS Directory Service is a replicated database directory that allows for a distributed directory. It's a sort of cluster spread across multiple computers that stores only the data of a directory and provides the particularity of dealing with failures.
It supports Microsoft Active Directory, OPENLDAP, Samba, identification and authentication (password + MFA), centralized resource management, and can make available to developers via Cloud Directory to respond to thousands of simultaneous calls.
In the case of more corporate activity, it is recommended to use Directory Service (Microsoft AD, Simple AD, AD Connector), which offers validation of network conflicts before implementation (CIDR) and allows for recording of who did what (CloudTrail).
Do not confuse Directory Service with Cognito, which is used for federated identity for mobile applications.
Amazon Inspector
AWS Inspector allows for the evaluation of vulnerabilities punctually or by scheduled cycles. It offers the following features:
- Target identification by tag (application).
- May require agents for certain controls (EC2 Linux, Windows).
- Definition of a model, rules, targets, time, and types of controls.
- Analyses of CVE (common vulnerabilities and exposures).
- Analyses of CIS benchmarks on OS security.
- Analyses of best practices in security.
- Analyses of RBA (runtime behavior analysis).
- Discovery reports with detailed elements and remediations.
Amazon WAF - Web Application Firewall
AWS WAF (Web Application Firewall) is an OSI level 7 application firewall that allows for identifying common attacks such as SQL injections and cross-site scripting.
It sits between clients and the web application, protects against DDoS attacks, and supports custom rules (conditions, ACLs, IP, chains). It can block or allow traffic based on chosen rules.
It works with the Application Load Balancer (ALB) for an internal AWS application and with CloudFront (HTTP, HTTPS, Edge Access). It also allows for securing a custom origin outside of AWS and records who did what with CloudTrail.

 English
English




